Identity theft and evasion loses governments, businesses and individuals billions of pounds in lost and stolen revenue. Information systems often hold vast amounts of data on individuals that could be used to reduce identity fraud.
In this article we’ll explore a conceptual solution to identity management.
There are many legislative implications to the proposal set out here. For the sake of simplicity, these implications are set aside.
There are many examination techniques used to establish an individual’s identity. Some are better than others. Common methods in use today include:
- Email/letter/call to address held on file
- Bank Account crediting
- Interview screening
- Circle of Trust
Once identity has been established to a probable extent, it is often necessary to retain this knowledge. Typically this is performed by issuing a “synthetic secret”, such as username and password; by issuing signed evidence, e.g. Membership/ identity card, passport, apostille, X.509, Kerberos or some other token; or by capturing information such as biometric information from the individual.
Verifying an identity
There are two common methods of verifying a subject’s identity.- “I am who I say I am”
- “I am who I say I am and he/ she says so too”
It seems unlikely that anyone’s identity can be established for certain. Therefore an identity could be given a score as to its likelihood to be the identity of the verification subject.
Individuals often have multiple personas, such as married names, nicknames, and adoptive names. Occasionally individuals change their persona altogether, such as transsexuals, criminals and witnesses. Therefore it would seem sensible for an identity to be composed of many personas, and since the identity is only ever probable, it would seem sensible to allow a persona to associate with many identities, as shown in Figure 1 and again in Figure 2 which presents the same idea using object relational modelling.
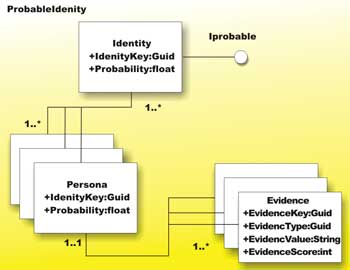
Figure 1: Probable Identity
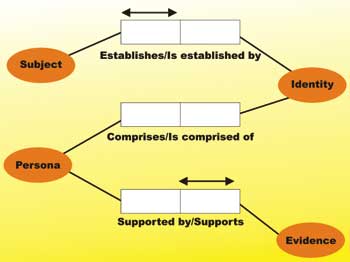
Figure 2: Probable Identity ORM view
As there are many ways of establishing (to a probable extent) an identity, so many forms of evidence are built up over time for a given persona. The more forms of evidence held against a persona, the greater the probability that the persona is valid.
A common issue in information systems is the issue of duplicate identities or “duplicate record syndrome”. This often results in costly data-cleansing exercises or workarounds such as record chaining and linking. I propose that multiple identities are embraced and accepted, and rated as to their likelihood to be the identity of the individual in question.
Thus, an individual may have established multiple identities. These identities may consist of one or more personae, each supported by one or more items of evidence.
An Identity Management Service
An identity management service would therefore provide two facilities – identity establishment and identity verification.Our identity establishment endpoint subcontracts the task of establishing an individual’s identity to the Establishment Actor, which could perform identity establishment in one or many ways. Figure 3 shows that in this instance the establishment actor uses an Identity Broker and the “Circle of Trust” paradigm, connecting to other Identity Management Services.
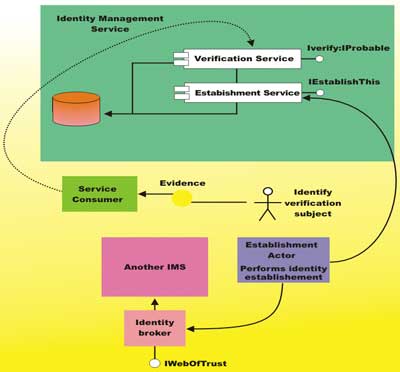
Figure 3: An Identity Management Service
Different Establishment Actors will establish an individual’s identity to varying extents of probability, and perhaps multiple Establishment Actors could be employed to establish an individual’s identity, increasing the probability of a valid identity being established.
It will never be possible to guarantee the veracity of an individual’s identity claim. Our identity verification endpoint depends on a two-way supply of evidence; from our identity verification subject and from our Establishment Actor in order to build an identity profile with a high probability of matching the identity claims of the individual.
The Circle of Trust
The circle of trust is a frequently used and I feel important identity verification technique. Confidence tricksters, cult leaders and other charismatic individuals often rely on isolating their targets in order to exclude them from a trusted peer group; this allows them to sponsor trust from their target, who might otherwise mistrust them based on peer feedback.By establishing a circle of trust that can be polled for feedback based on the claims evidenced by the individual, the probability that the claim is valid can be further boosted (or denied).
Conclusion
An individual’s claim to an identity will never be fully trustworthy. By accepting that as fact and working with multiple probable identities for an individual, significant gains could be made in the management of the risk associated with identity verification. The goal should be to offset the risk to the information or assets under safeguard with the probability that the individual can be held accountable for their actions through their claimed identity.Robbie Gibbon is an Enterprise Architecture practitioner in the Banking, Health, and Government sectors, specialising in Systems Integration based around the SOA paradigm.
Terminology
- Establish – To identify an individual. To associate an identifier with an individual.
- Verify – To authenticate the identity claims of an individual.
- Evidence – Artefacts offered in support of an identity claim.
- Persona – A collection of related evidence that forms a pseudo-identity. An Identity may be constructed of a number of personae.
Comments